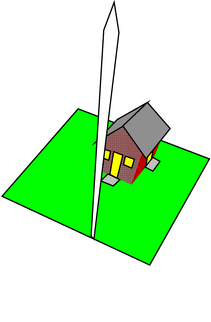
Figure 1: The One-Picket Fence
Copyright © 2007 jsd
I learned the following parable from Neal Stephenson, who attributed it to Bruce Schneier (reference 1):
Once upon a time a guy decided to build a picket fence around his property, in order to achieve security. The result is shown in figure 1. The entire fence consisted of a single picket, three inches wide and a mile high:
“Ha!” he said. “Nobody is going to hop over that.”
The problem is that this picket provides no security at all. Sure, nobody can hop over it, but they can easily go around it, and the front door is standing wide open. For that matter the side door and the windows are open, too.
There are two main ways that such a “fence” can come about:
This is of course related to the proverb that a chain is only as strong as its weakest link.
Another way of expressing the same idea is in terms of threats in parallel and defenses in series, as shown in to figure 2 and figure 3.
The point is that we need to defend against all plausible attacks. We need to solve the whole problem. It makes no sense to add extra defenses in series in an area that is already well defended. What we need are more defenses in parallel, defending areas that have not heretofore been well defended.
This parable applies to Pima County as follows: the Division of Elections has a number of problems, one of which is a fixation on preventing attacks by outsiders. They have erected a mile-high one-picket defense against such attacks. “Ha!” they say, “Nobody is going to hop over that.”
Alas, this leaves the system wide open to attacks by insiders. There is a severe lack of balance. There is an appalling failure to solve the whole problem. You can understand the situation at a glance by reference to figure 2.
I’m not saying that protection against outsider attacks is unnecessary or bad; I’m just saying that it is no substitute for protection against other lines of attack.
The Pima County Democratic Party and other observers have asked the county to release records of votes cast in previous elections. This would make the system as a whole more secure, as shown in figure 3.
So far, the county has refused to make the databases available. This has become the subject of a lawsuit. Extensive reporting on the trial can be found in reference 2.
First of all, the county’s claim is false because good defenses against outsider attack already exist (and if needed, more could be arranged). Keeping the database secret therefore confers only an imaginary degree of additional security.
Secondly, even if we temporarily and hypothetically imagine that secrecy provided a little bit of security against outsider attacks, the county’s argument would still be diametrically false, because it fails to consider the system as a whole. Outsider attacks are not the only threat nor even the most dangerous threat. As shown in figure 3, the overall result is better if we move some strength from an area that doesn’t need it to an area that does.
It is very important to appreciate that figure 3 describes a situation that is less vulnerable, in relative terms.
One should not imagine for a moment that it is invulnerable in absolute terms.
Making the voting results open to public inspection (after the close of the election) is necessary but not sufficient. It is only one of many, many steps that need to be taken before the system has any semblence of real security.
As one small example, in addition to the voting records narrowly construed, the tabulation machine logs should be released. Right now this is a semi-moot point, because Diebold stores operational logs and voting results in the same database. Still, the point remains that if/when the logs and the voting records are available separately, both should be released.
Diebold requires its programs to be kept secret. Pima County has argued that the election results database is a “program”.
This argument has two fatal flaws.
For one thing, the state of Alaska uses similar machines, and routinely releases the database. There have been no complaints from Diebold. From this we infer that Diebold does not consider the database to be a program. (We might also note that there have been no reported adverse effects on the security of Alaskan elections.)
Secondly, Federal law requires voting machines to be certified, and the certification standards forbid any kind of programs that can be modified in the field, i.e. modified after certification. Since the database manifestly needs to be modifiable, either it is not a program, or the whole system is uncertifiable and unfit for use.
You can’t have it both ways: either you decide the database is a program and stop using the machines entirely, or you decide the database is not a program and stop using using this as a pretext for keeping the database secret.
Section 2 raises some additional points about secret programs and methods.
There is a proverb that says you should never support a strong argument with a weaker one. However, if we ignore that advice, we discover some weak arguments that could be made in this case. I don’t want to emphasize them, but it might be nice to mention them just for completeness.
In almost all attack scenarios, the attacker would need to read the current database, make modifications, and write the modifications back into the database.
You might think that being able to “practice” on prior versions of the database would give the attacker an advantage, but in fact any such advantage is vanishingly small. Since the Diebold machines use a standard database format, the same format used by Microsoft Access, the attacker is already able to get plenty of practice. (Even if the format were nonstandard, the attacker could still practice on the Alaskan data. There is no point in locking the barn door, since this horse has been gone for a long, long time.)
There is a mirror image to this argument that one sometimes hears: If the system is so insecure that releasing the data from past elections is problematic, the system is so insecure that it should never have been used in the first place. You should release all the data from old elections, and fix whatever the problem is before the next election ... even if that means ripping out the existing system and installing something decent in its place. That’s all true, that’s the correct decision, and it probably describes what’s going to happen ... but I’m not sure it is the best way to motivate the correct decision.
Consider the following well-known examples, to name just a few:
These guys tampered with classified information on a grand scale. They did not do it from the outside. They did not smash locks. They did not overpower guards.
These guys were granted access to secure areas, and then abused their privileges. The internal controls were not adequate to prevent abuse.
Kim Philby said it himself: “To betray, you must first belong”.
Reference 13 discusses insider threats.
It is interesting that Diebold makes such a fuss about keeping secret the programs in their voting machines.
This makes them a laughingstock in the cryptography and security community. It has been appreciated for 125 years that in a properly-designed security system, the keys and passwords should be the only secrets; there should be no need for secret software or secret methods. To say the same thing the other way, any system that requires its methods to be kept secret is fundamentally unsound. This is known as Kerckhoffs’s Principle, or more particularly Kerckhoffs’s Second Principle. This originated in reference 3. For an overview, see reference 4.
To repeat:
The problem is, the bad guys will notice weaknesses in the system. An outsider only needs to steal or borrow one voting machine, somewhere in the world, and reverse engineer it. And an insider has innumerable opportunities to reverse engineer the system, looking for weaknesses.
In fact, when it comes to Diebold machines, the weaknesses are so obvious that no reverse engineering is needed. A landmark study of weaknesses in one Diebold product line can be found in reference 5. See also reference 6.
A more recent analysis can be found in reference 7. Its Appendix A lists 126 separate “flaws” in the Diebold equipment. On page 26 it lists 37 of these as “fixed” and another 37 as definitely not fixed; the status of most of the others is not clearly stated. Another recent analysis can be found in reference 8.
To put this in perspective, it helps to realize that for many years, in Australia there has been a Linux-based electronic voting system, where every detail of the system is open to public review. See reference 9 and reference 10. This makes quite a dramatic contrast with Diebold’s stated "need" for secrecy.
One of the documents produced at trial is a 60 page memorandum from County Administrator C.H. Huckelberry to the Board of Supervisors. The last 20 pages reproduce an article from The Information Technology & Innovation Foundation, “Stop the Presses: How Paper Trails Fail to Secure e-Voting”. The article one-sidedly favors cryptologic solutions to all problems, which is unfortunate; a more balanced approach would have been preferable. Even if you accept the general drift of the article, you are left with many questions, including questions about its relevance. The article suggests techniques such as cut-and-choose and zero-knowledge proofs. These techniques are incomparably more sophisticated than the methods the Diebold machines are currently using, so the impact of these suggestions will not be felt any time soon, if at all.
At trial there was some discussion of the fact that the data from one recent election is (at present) lost, in the sense that (at present) nobody can find it.
On cross examination, the point was made that we cannot prove that anybody in particular lost it. We cannot prove that it is “missing” from the box where it was expected to be, because we cannot prove that it was ever in that box.
Well, that’s just the point. The fact that nobody can account for such things indicates a serious lack of professionalism.
Arguing that we cannot prove criminal wrongdoing on the part of any particular person is a great line of defense in a criminal trial, but the standard of “no provable criminality” is not the standard we should demand of the Department of Elections.
We are talking about failure to protect critical records, and failure to account for critical records when they are shipped out or shipped in. We are talking about the Division of Elections, where the whole raison d’être is to produce and protect reliable records of elections. Somebody needs to show some professionalism. Somebody needs to stand up and take responsibility for making sure losses like this cannot happen.
As you can see in figure 4, even when behavior is “not provably criminal” it can still be a long way from meeting acceptable standards of professionalism.
Security of the polling places is important. Security of the central tabulation facilities is important. But still we need a balanced approach, which requires looking at additional issues.
There is major potential for vote-buying, voter intimidation, and voter coercion associated with mail-in ballots including absentee ballots. (In contrast, polling-place procedures have over the years evolved to have a fair degree of resistance to such threats.)
This is a major issue. Mail-in ballots, before they are mailed, are largely outside the purview of the Division of Elections strictly speaking, but the overall balloting system is still within the purview of the County and State government.
Again, there needs to be a balanced analysis of the system as a whole.
The Pima County Division of Elections has put out a notice “to solicit input regarding the Pima County Election Security Plan.”
A discussion of this “plan” can be found in reference 12.
If the Pima County Division of Elections had an ounce of sense, they would cheerfully make available the database of each election’s results, and other things such as audit logs, as soon as they become available after the close of the election.
The Diebold machines are very insecure, and should be replaced ASAP by something more secure, preferably something that upholds Kerckhoffs’s Principle, i.e. something where even the programs and methods are open to public review.
Copyright © 2007 jsd