Figure 1: Threats, with or without Database Release
Copyright © 2007 jsd
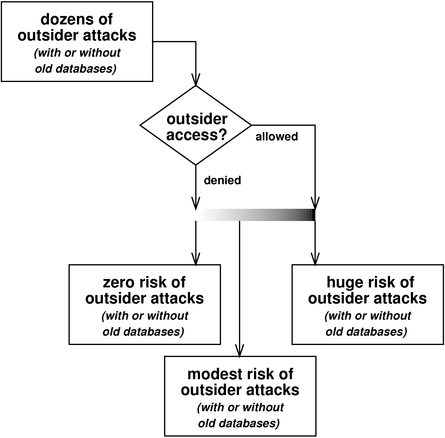
The question for today is this: How much harm would be done by releasing the databases containing records of past elections? We can answer this question with the help of figure 1.
We start with the observation that there are dozens of known security problems with the Diebold system, including the polling-place machines as well as the central “GEMS” tabulating machine. This is documented in reference 1.
There is some hope of eliminating these problems in the long run, by replacing the Diebold system with something decent, but in the medium term and especially in the short term, the only defense is to rigorously prevent outsiders from getting access to the systems.
If outsider access is allowed, there are horrific problems, whether or not the outsiders have seen the databases from past elections. That’s because attackers are interested in the current database, not old databases. Any attacker will look at the current database, change it, cover his tracks, and leave. There is nothing an attacker can learn from old Pima County databases that could not be learned by studying already-released databases from other jurisdictions.
At the other extreme, if outsider access is denied, there is no problem, whether or not outsiders have seen the databases from past elections.
Reality presumably lies somewhere between these two extremes. As shown in the figure, there is a grayscale between unlimited outsider access and perfect protection against outsider attacks. That is, there will always be some slight risk of penetration by outsiders. However the point remains that this risk is the same whether or not the outsiders have seen the databases from past elections.
I am not saying the total risk is zero. I’m just saying that the percentage of the risk attributable to release of the database is zero.
FWIW I think the total risk is distinctly nonzero. Still, the point releasing the databases cannot make things worse, and will certainly make things better.
To make the same point the other way around, if the system is so flaky that it cannot be operated with acceptable security following the release of old databases, it is so flaky that it should never be used at all.
Some people have put forth the theory that the databases might contain evidence of criminal wrongdoing. In such a case there would be an obvious motive to keep the databases secret, at least for a few years, so as to run out the clock on the statute of limitations.
I do not put much stock in this theory, for a couple of reasons. First of all, if there had been clear evidence of wrongdoing, the recent investigation by the State Attorney General would probably have found it. Secondly, as pointed out in reference 5, it is likely that an insider attack would leave no traces anyway.
Other people have lesser suspicions, namely that the databases might contain evidence of non-criminal incompetence. This would provide a motive to keep the databases secret. I don’t know what to say about this, except to say that it would be highly improper to use such considerations as a reason to keep the databases secret. Yes, it is human nature to want to keep them secret, but no, it is not legal.
The purpose of the public-records laws is precisely to prevent future wrongdoing by exposing past wrongdoing.
Copyright © 2007 jsd